802.11b WEP Let's break 802.11b WEP
Bugs in 802.11b WEP and let’s break it!
Contents
Intro
Below is the picture describing the algorithm for 802.11b WEP.
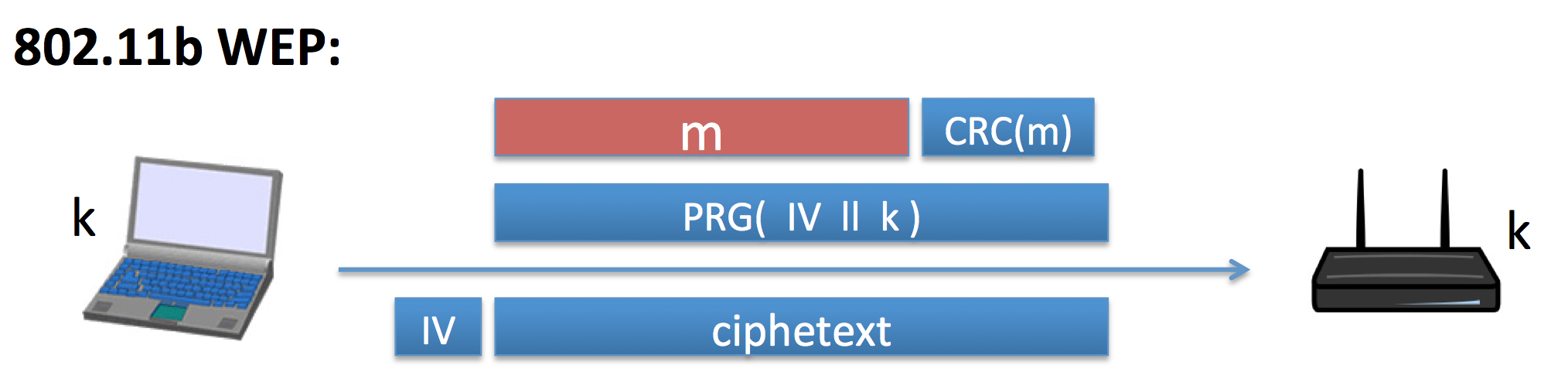
Main points
- CRC(m) is the checksum of MESSAGE m, here it’s not important so do not care.
- IV is 24-bits string, increasing by every frame from 0 and k is a 104-bits string so the total length is 128.
-
PRG is a pseudorandom generator algorithm and the input is IV k , means concatenation. - The receiver receive the ciphertext, plus a IV in front of ciphertext and apply the decoding algorithm.
BugI-limited IV
The limited 24-bits IV
802.11b WEP algorithm uses a 24-bit length IV, which means we have only unique frame numbers. That means every 16million frames we will obtain the same keys, under such condition we could apply a two-time pad attack.
BugII-Powercycle
Powercycle
Every powercycle IV will reset to 0.
As a result, we could get a lot frames with IV set to 0.
Under such circumstances, we could also apply two-time pad attack.
BugIII-Related keys
RC4
PRG in WEP use a algorithm called RC4
| key for frame #1: (1 | k) |
| key for frame #2: (2 | k) |
and so on. These keys are related, they are almost the same. And after processed by RC4, we could also find some relation.
Attack
Fluhrer,Mantin ans Shamir in 2001 found that after Later others proposed better method shows
blog comments powered by Disqus